"Enhancing AWS Deployments Security: Leveraging OpenID Connect (OIDC) with GitHub Actions"
Let us first know what is Open ID Connect (OIDC):
OpenID Connect (OIDC) is a widely used authentication protocol that allows users to log in to different websites and applications using their existing accounts from a trusted identity provider (such as Google, GitHub, or Microsoft). It provides a secure and standardized way for applications to verify the identity of users.
Importance and Needs:
Single Sign-On (SSO): OIDC enables Single Sign-On, allowing users to access multiple services with a single set of credentials. This reduces the need to remember multiple usernames and passwords.
Security: By relying on trusted identity providers, OIDC improves security. User authentication is handled by providers with robust security measures, reducing the risk of unauthorized access.
User Experience: Users can access various applications seamlessly without repetitive logins, enhancing the user experience.
Standardization: OIDC follows an open standard, making it easier for developers to implement and integrate authentication across different platforms.
Integration: In industries, OIDC is crucial for secure access to applications, APIs, and cloud resources. It's used to authenticate users, applications, and devices, ensuring that only authorized entities can access sensitive data and services.
Compliance: Many industries have regulatory requirements for secure authentication. OIDC helps organizations meet these compliance standards by providing a standardized and secure authentication method.
Overall, OpenID Connect plays a vital role in enhancing security, user convenience, and interoperability in modern digital environments, making it a valuable asset across industries.
Let's Start With Our Project:
First, Create a GitHub repository and copy the git clone link.

Open your terminal or VS Code and run the git clone command with the clone link

Next, we will set up an open id connect in our AWS Account,
Go to - Security Credentials or you can simply go to IAM

Now, from left panel select - identity providers

Here, select Add provider

Open a new tab and search for "GitHub docs for AWS identity provider"
You will see the provider URL and Audience we need both to setup OIDC

After selecting "Add provider" now select - Open ID connect and copy - paste the provider URL and Audience and select " Get thumbprint "

After selecting thumbprint - you might get this notification from AWS,but nothing to don't worry

Click - add provider

As we can see our provider is added

Select the GitHub provider - just to check it out

Now, the next step is to create an IAM Role for the provider - select roles on the IAM section and select " Create role "

Here, select " Web identity "

Scroll down and select the provider token for GitHub

Here we have to select the provider token and audience that we have previously and along with that also provide - a Github username in the " GitHub organization section ", give the GitHub repository name and at last, specify the branch - in our case, it is " main "

Next, is to select the " role policy " Here for demo project purposes I have selected " Administrator Access" which is not recommended in real case scenarios

Next, is to specify the name of the IAM Role and select " create "

Our IAM role is created

Next, we go to our IAM role and go to " Trust relationship " so that we can make changes in the permission policy.
Here I have an additional condition in String equals - for pull_request, I have provided the syntax make sure to edit your changes before apply

{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::9945510650066:oidc-provider/token.actions.githubusercontent.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"token.actions.githubusercontent.com:sub": [
"repo:amitkmr076/Github-OIDC-AWS-Demo:pull_request",
"repo:amitkmr076/Github-OIDC-AWS-Demo:ref:refs/heads/main"
],
"token.actions.githubusercontent.com:aud": "sts.amazonaws.com"
}
}
}
]
}
Now, we will create an S3 bucket so that we can upload files through GitHub action for our demo project.
Provide the bucket name and create

Our bucket is created

Inside our GitHub-oidc bucket, we see its empty

Now let's go to our terminal and create some files.
As our repo is cloned and inside the folder, we created a simple file " name.txt " and added some content to it

Now, open the IAM role we created and copy the arn link

Next, we will create a new folder named " .github " inside our project folder, and inside the .github folder create another folder named " workflows ", and inside the workflows folder create a "main.yml" file as our GitHub action configuration file.
Here copy and paste the IAM role arn in the " role to assume " syntax and also copy and paste your S3 bucket name run syntax to copy our files to the S3 bucket and also make sure to correctly specify your AWS region

name: AWS OIDC Connect Demo
on:
push
env:
AWS_REGION: "us-east-1"
permissions:
id-token: write
contents: read
jobs:
DemoOIDC:
runs-on: ubuntu-latest
steps:
- name: Git clone the repository
uses: actions/checkout@v3
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v1
with:
role-to-assume: arn:aws:iam::391036601714:role/github-action-oidc-role
role-session-name: samplerolesession
aws-region: ${{ env.AWS_REGION }}
- name: Upload files to S3 bucket
run: |
aws s3 cp . s3://gtihub-oidc-demo-bucket/ --recursive --exclude ".git/*"
After adding all the files do the git status command to see the changes

Now, git add and git commit and finally push the changes to the GitHub repository

Our files are uploaded successfully

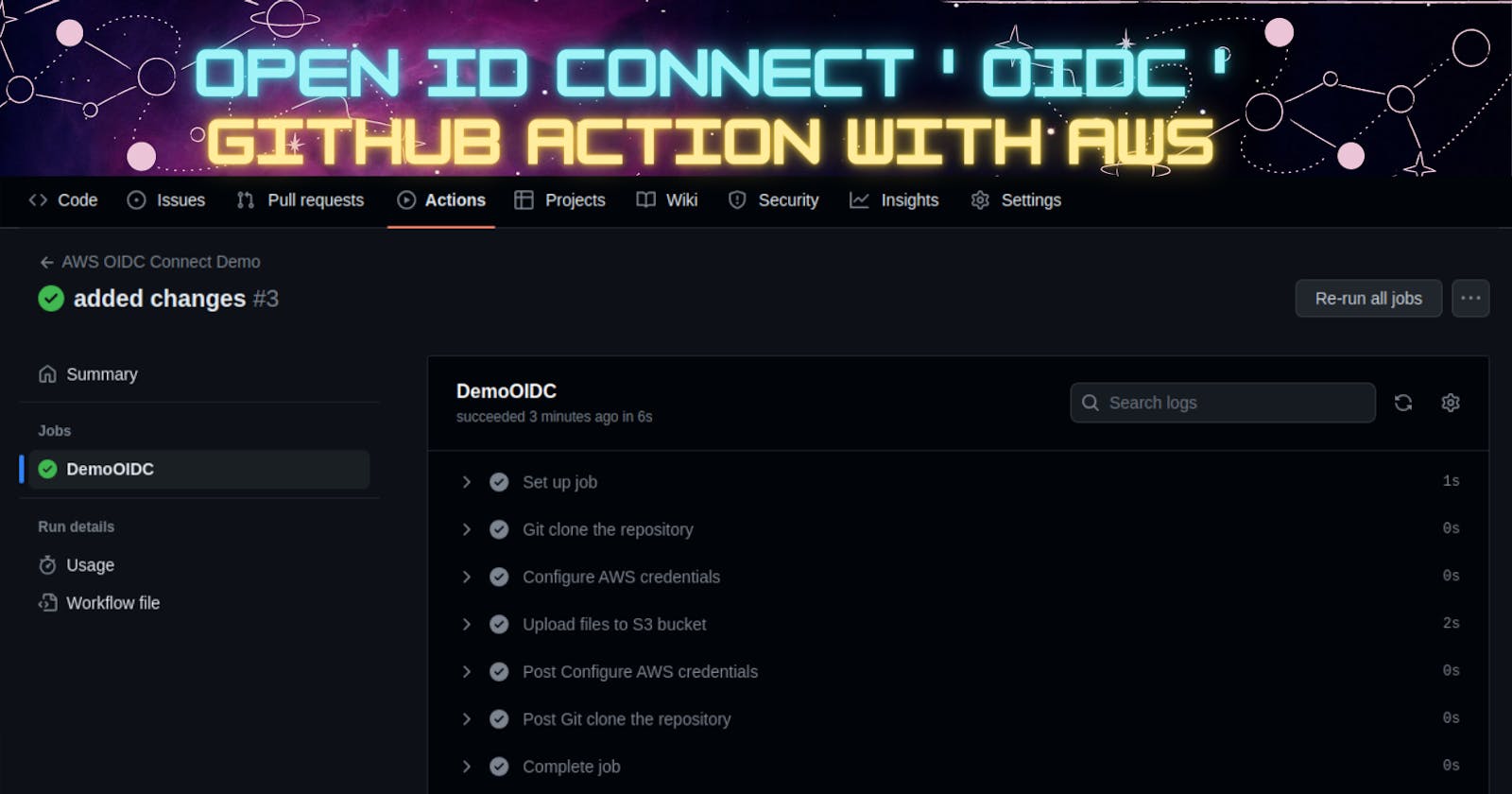
Let's see if our GitHub action is been triggered or not.
Our GitHub action workflow is triggered successfully and passes all the checks and performed all jobs.
This was the 3rd push that was successful as you all can see last 2 pushes failed of some syntax error in the YAML file

Select the workflow to check the steps

Here we can see all the jobs were successfully performed and also pushed our files to the S3 bucket, let's check

And finally, we can see our all files are being uploaded to the S3 bucket through the GitHub action workflow

Remember in this project we didn't use any AWS credentials for the Access key and Secret key to access AWS and deploy our project - All is being done through Open ID connect.
It was a fun project to do and to learn as well I hope you all gain something and some insight from the project and the article.
Thank you for your interest in reading the article we really appreciate your readership!!!